Apple wants to make your macOS and iOS devices even more secure. The tech giant has filed for a patent (number 9,639,673) for “protecting software through a fake crytographic layer.”
In the patent filing, Apple notes that software developers invest considerable resources in the development and maintenance of computer software. This investment often results in the development of proprietary algorithms that are advantageous over those used by the competition and which the developer would like to keep secret so as to leverage the superiority of the algorithm. In addition to proprietary algorithms, software may also contain embedded secrets such as cryptographic keys. Because of the plethora of important information, software is often the target of various reverse engineering efforts to dissect, analyze, and discover how it works.
To minimize reverse engineering efforts, attackers often attempt to locate higher value code by identifying known code patterns or characteristics. To increase the reverse engineering effort, software developers have applied various protection mechanisms that attempt to hide or disguise high value code.
For example, a software developer may apply one or more code obfuscation techniques to a cryptographic routine to disguise known code patterns. Apple says that such techniques can be successful at increasing the effort required to reverse engineer a section of code, but they can also have negative side effects, such as decreasing performance. Additionally, the company says they may not be applied uniformly across the program so an attacker may still be able to classify sections of code as lower and higher value even if the class of higher value code is larger than it would have been without the obfuscation. Apple wants to alleviate this problem.
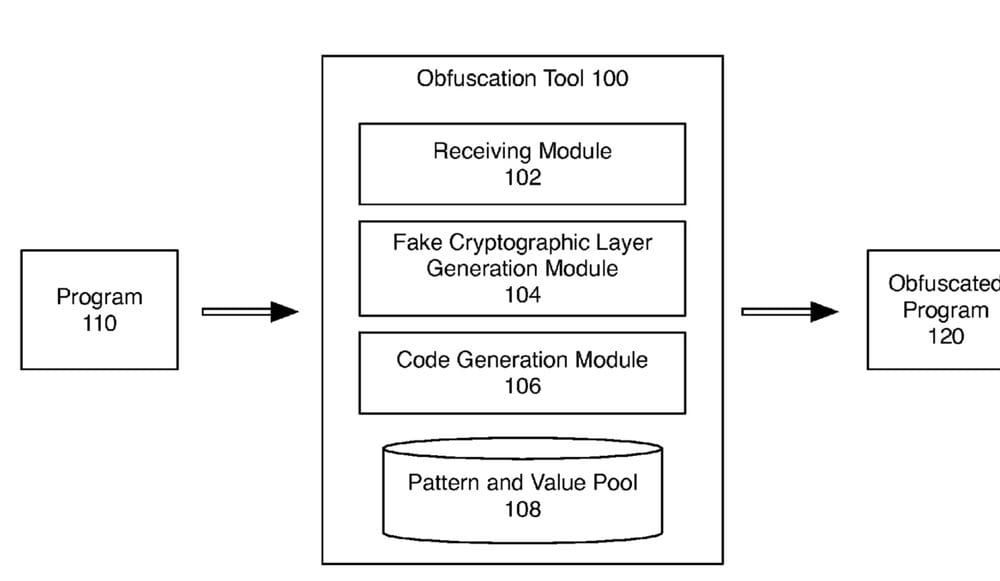
Here’s a summary of the patent: “The fake cryptographic layer obfuscation technique can be used to lure an attacker into expending reverse engineering efforts on sections of code the attacker would normally ignore. To do this the obfuscation technique can identify sections of code that are likely to be of lesser interest to the attacker and disguise them as higher value sections.
“This can be achieved by transforming a lower value section of code to include code patterns, constants, or other characteristics known to exist in sections of code of higher value, such as cryptographic routines. To transform a code section, the obfuscation technique can use one or more program modifications including control flow modifications, constant value adjustments to simulate well-known cryptographic scalars, buffer extensions, fake characteristic table insertion, debug-like information insertion, derivation function-code generation linking, and/or cryptographic algorithm specific instruction insertion.”
Of course, Apple files for — and is granted — lots of patents by the U.S. Patent & Trademark Office. Many are for inventions that never see the light of day. However, you never can tell which ones will materialize in a real product.
