WatchGuard Technologies, which specializes in network security solutions, has issued its quarterly Internet Security Report for Q4 2018. It found that network attacks targeting a vulnerability in the Cisco Webex Chrome extension increased in popularity dramatically, rising to be the second-most common network attack after being almost nonexistent in early 2018.
Phishing campaigns showed a dangerous increase in sophistication in quarter four (Q4), with new attacks utilizing advanced methods such as threatening to release recordings of users visiting adult content online, customizing emails for specific targets and creating fake banking login web pages, according to WatchGuard. Based on data from tens of thousands of active WatchGuard Firebox appliances around the world, the complete report examines the top malware and network attacks targeting mid-market businesses and distributed enterprises today.
“There was a noticeable increase in advanced phishing attacks targeting high-value information this quarter,” said Corey Nachreiner, chief technical officer at WatchGuard Technologies. “Now more than ever, it’s vital for businesses to take the layered approach to security, and deploy solutions like WatchGuard’s DNSWatch that offer DNS-level filtering designed to detect and block potentially dangerous connections and automatically refer employees to resources that bolster phishing awareness and prevention. A combination of security controls and human training will help businesses avoid becoming hooked by phishing attacks.”
The top takeaways from the Q4 2018 report include:
New network attack targets Cisco Webex Chrome extension. A new network attack targeting a remote code execution vulnerability in the Chrome extension for Cisco Webex exploded in popularity last quarter. This vulnerability was disclosed and patched in 2017, but WatchGuard detected almost no network attacks targeting it until now. Detections grew by 7,016% from Q3 to Q4. This spike shows just how important it is to install security patches as soon as they are available.
New customized “sextortion” phishing campaign on the rise. A new “sextortion” phishing attack was the second-most common attack that our malware engines detected in Q4 2018, mainly targeting the Asia-Pacific region. It accounts for almost half of all of the unique malware hashes detected in Q4 because the email phishing message is tailored to each recipient. The message claims the sender has infected the victim’s computer with a trojan and recorded them visiting adult websites. It threatens to send these compromising images to their email contacts unless they pay a ransom. WatchGuard saw a significant amount of this malware in Q4 and all users should be on the lookout for these fake emails.
16.5% of all fireboxes were targeted by CoinHive cryptominer. The most widespread malware variant in Q4 came from the popular CoinHive cryptominer family, showing that cryptomining remains a popular attack type. Two of the top ten most common pieces of malware detected in Q4 were also cryptominers, carrying over from past quarters.
A major phishing attack leverages a fake bank page. Another widespread piece of malware in Q4 sent a phishing email with a fake, but highly realistic Wells Fargo login page to capture victim emails and passwords. Overall, WatchGuard saw a rise in sophisticated phishing attacks targeting banking credentials in Q4.
One ISP’s filtering error routed Google traffic through Russia and hina for 74 minutes. The report includes a technical analysis of a Border Gateway Protocol (BGP) hijack in November 2018 that inadvertently sent most of Google’s traffic through Russia and China for a short time. WatchGuard found that a Nigerian ISP called MainOne made a mistake in their routing filters, which then spread to Russian and Chinese ISPs and caused much of Google’s traffic to be routed through these ISPs unnecessarily. This accidental hijack highlights how insecure many of the underlying standards that the internet is based on are. A sophisticated attack targeting these flaws could have potentially catastrophic consequences.
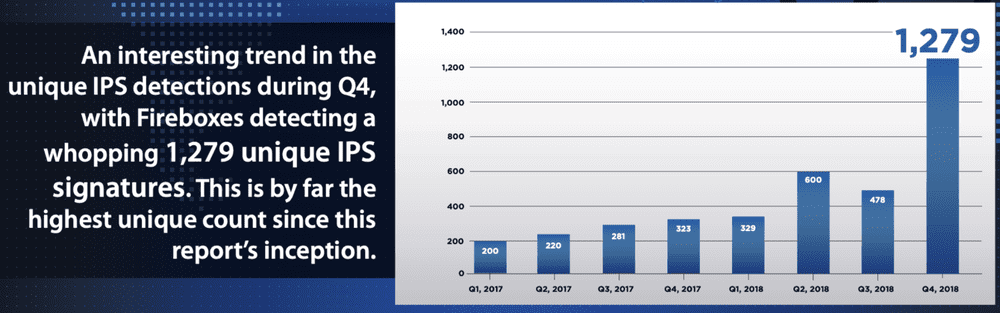
Network attacks rise after historic lows in mid-2018 – Network attacks rose 46 percent by volume and 167% in terms of unique signature hits in Q4 compared to Q3. This follows a trend seen in previous years with attacks ramping up during the holiday season.
These finding are based on anonymized Firebox Feed data from over 42,000 active WatchGuard UTM appliances worldwide. In total, these Fireboxes blocked over 16 million malware variants (382 per device) and approximately 1,244,000 network attacks (29 per device) in Q4 2018.
For more information, download the full report here.
