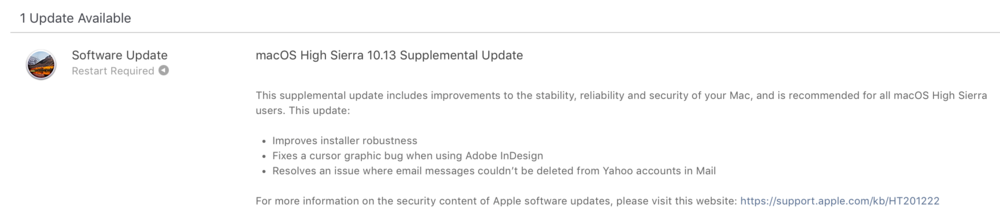
Well, that was fast. Earlier this morning we posted an article about a flaw in macOS High Sierra that exposed passwords for APFS encrypted containers; now a supplemental update has been released to fix that issue and it’s available in the Mac App Store. In addition to two security fixes, the Supplemental Update also “improves installer robustness”, “fixes a cursor graphic bug when using Adobe InDesign”, and “resolves an issue where email messages couldn’t be deleted from Yahoo accounts in Mail”.
The update actually fixes another security issue as well, as noted in the text following from Apple:
StorageKit
Available for: macOS High Sierra 10.13
Impact: A local attacker may gain access to an encrypted APFS volume
Description: If a hint was set in Disk Utility when creating an APFS encrypted volume, the password was stored as the hint. This was addressed by clearing hint storage if the hint was the password, and by improving the logic for storing hints.
CVE-2017-7149: Matheus Mariano of Leet Tech
Security
Available for: macOS High Sierra 10.13
Impact: A malicious application can extract keychain passwords
Description: A method existed for applications to bypass the keychain access prompt with a synthetic click. This was addressed by requiring the user password when prompting for keychain access.
CVE-2017-7150: Patrick Wardle of Synack
New downloads of macOS High Sierra 10.13 include the security content of the macOS High Sierra 10.13 Supplemental Update.
